The writer's first language is NOT English. Pardon me for grammar and spelling mistakes.
Data Lab
Todo...
Bomb Lab
Like most people, I use Windows for most time, but this lab require a Linux environment. Therefore, WSL2 is recommend here.
If you haven't try it, follow this article to install WSL2 on you machine.
To easily reed code and disassemble them, you need to install VSCode and IDA on your host system.
Now, we need to download the lab file...
1 2 wget http://csapp.cs.cmu.edu/3e/bomb.tar
And install dependencies for the lab.
1 sudo apt-get install build-essential gcc-multilib gdb
If you are not familiar with gdb, gdbgui could be a good choice.
Now, copy the executable file to your desktop, using IDA to open it, and I'm sure you are ready to solve it. :)
Phase 1
IDA Assembel View
Now, tap the magical "Tab" button.
IDA C-Style View
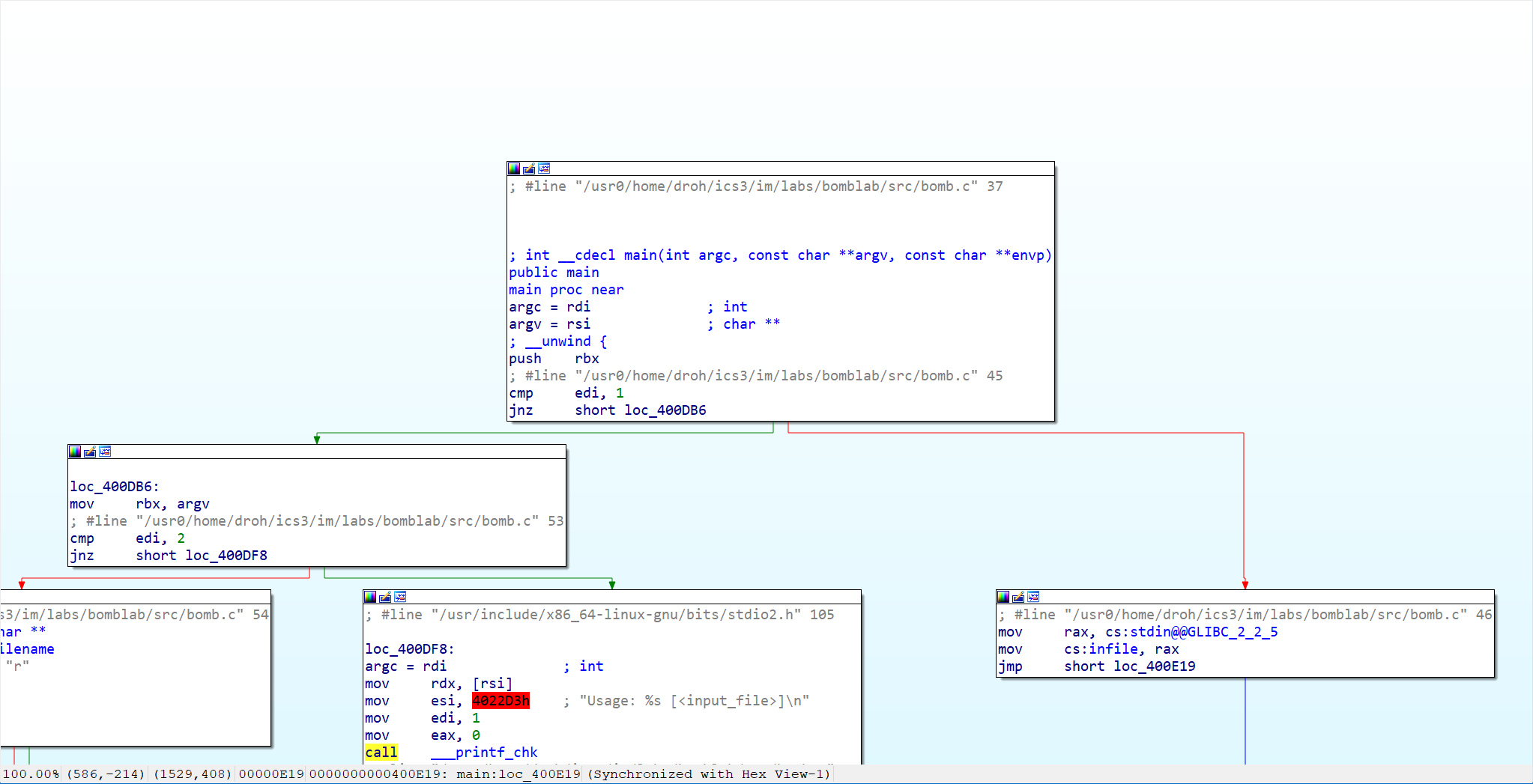
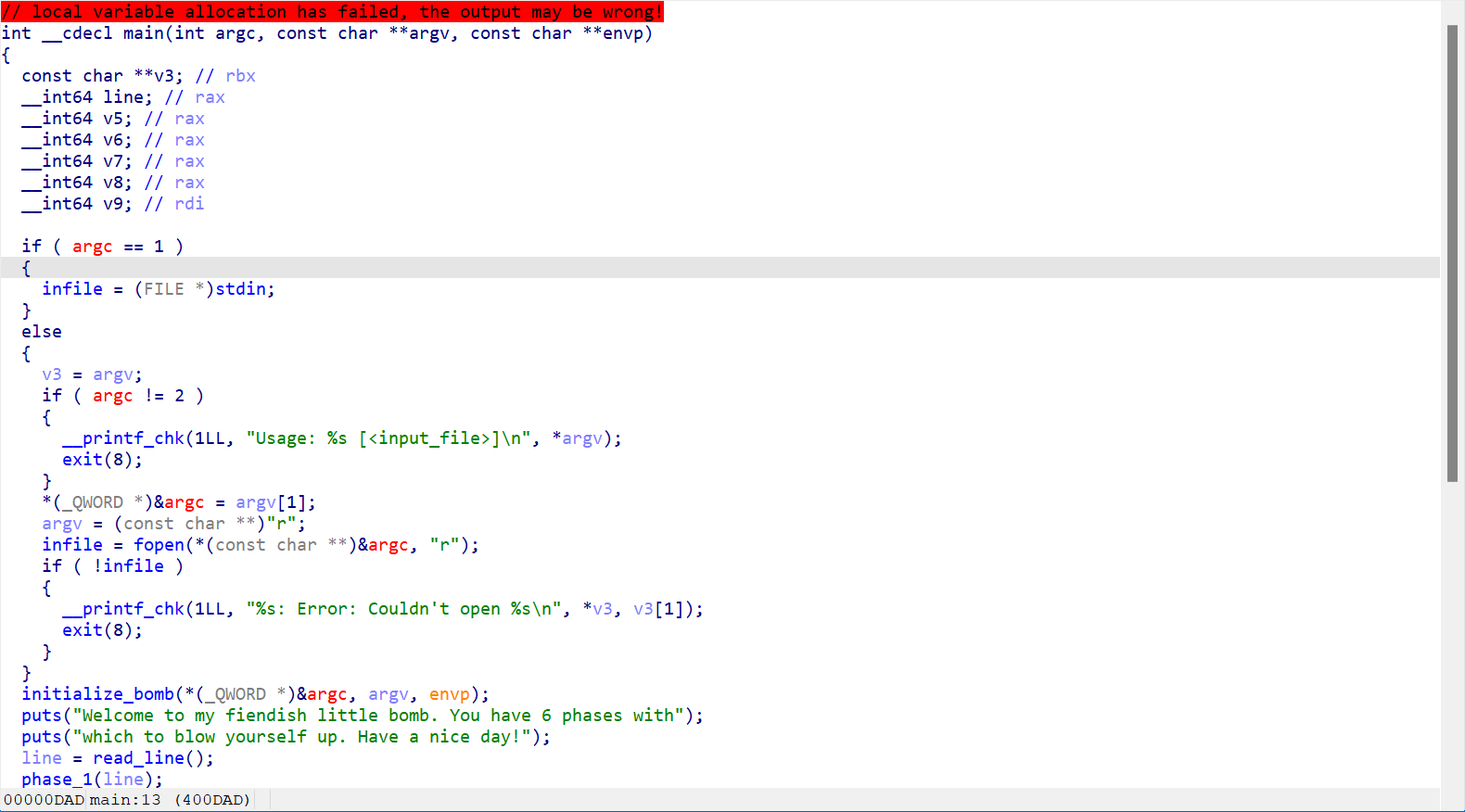
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 int __cdecl main (int argc, const char **argv, const char **envp) const char **v3; if ( argc == 1 )stdin ;else if ( argc != 2 )1LL , "Usage: %s [<input_file>]\n" , *argv);exit (8 );1 ];const char **)"r" ;const char **)&argc, "r" );if ( !infile )1LL , "%s: Error: Couldn't open %s\n" , *v3, v3[1 ]);exit (8 );puts ("Welcome to my fiendish little bomb. You have 6 phases with" );puts ("which to blow yourself up. Have a nice day!" );puts ("Phase 1 defused. How about the next one?" );puts ("That's number 2. Keep going!" );puts ("Halfway there!" );puts ("So you got that one. Try this one." );puts ("Good work! On to the next..." );return 0 ;
This is more like it.
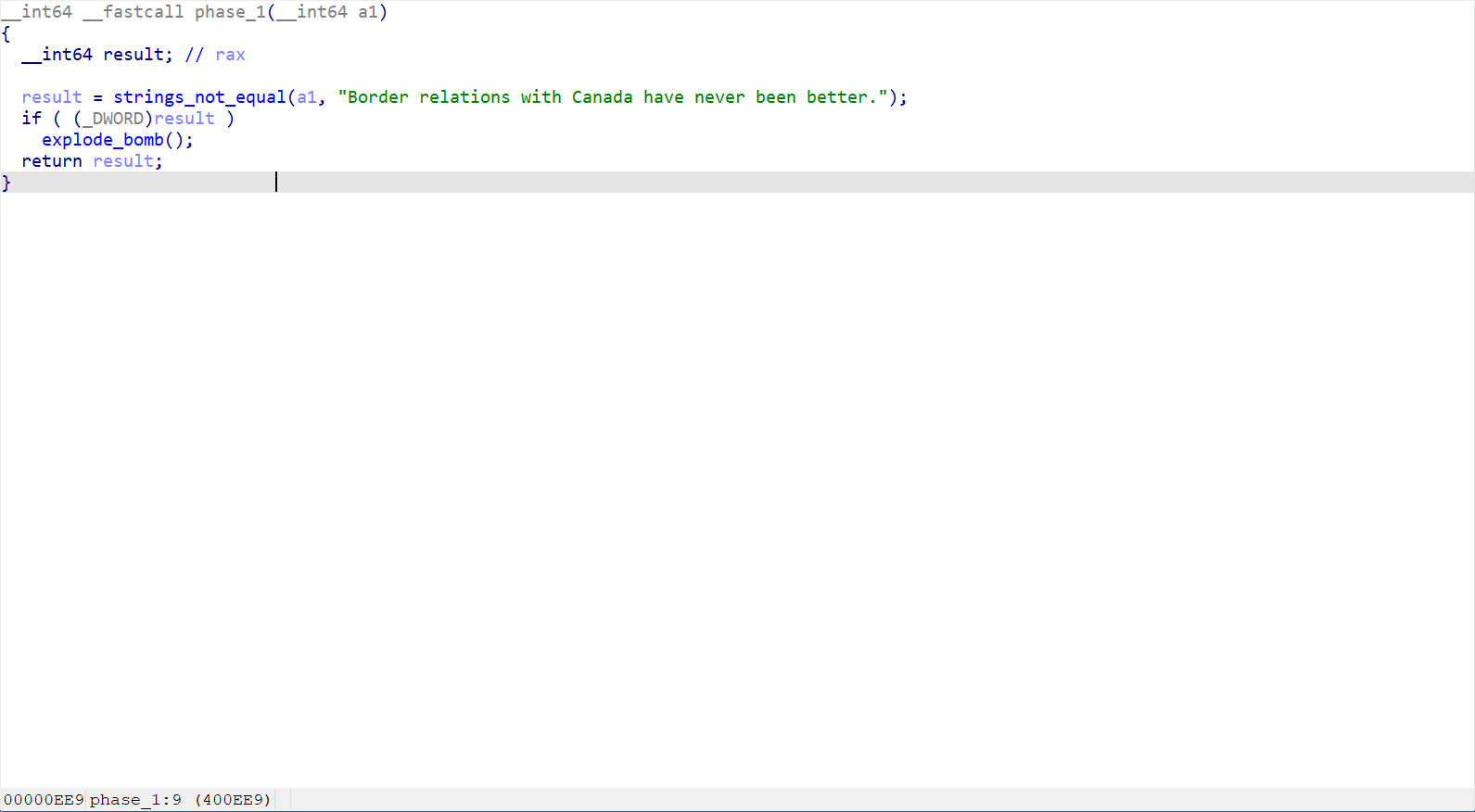
Step into the phase_1() function.
phase 1 disassemble
"Border relations with Canada have never been better."
Phase 2
Move in to function phase_2.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 __int64 __fastcall phase_2 (__int64 a1) char *v2; int v3; char v4; char v5; if ( v3 != 1 )do unsigned int )(2 * *((_DWORD *)v2 - 1 ));if ( *(_DWORD *)v2 != (_DWORD)result )4 ;while ( v2 != &v5 );return result;
NOTE: The type of a1 is obviously not _int64 , it should be a char* as it refers to the user input string.
From the IDA giving information, v3 should be a stack allocated int array, and we could reasonably assume that the function read_six_numbers will read six numbers and store them in array v3.